Did you know? In 2018, 62% of businesses experienced phishing and social engineering attacks. In 2019, on an average 4000 ransomware attacks took place everyday. E-commerce websites are particularly attractive for hackers because of the numerous financial transactions that occur daily through an e-commerce website.
Thus, security is a major concern for all online businesses and Magento users are no different. So, we have composed this article to summarize all Magento 2 security best practices that every website owner should follow.
Magento 2 Security Best Practices
1. Protect Magento Admin
The admin panel in Magento helps the website owner to administer their website efficiently. An unsecure Magento admin panel is an open invitation to hackers. By gaining access to the admin panel hackers can hijack your whole website operations. They could deface your website, steal/modify data, inject malware, redirect your store, host malicious and offensive content and what not!
Here is how you can increase Magento Security by securing the admin panel:
a. Change Default Admin URL
Every Magento installation has a preset default URL http://example.com/magento/admin. Since this admin path is widely known, it should be changed to avoid getting hacked. Here is how you can change the Admin panel URL for additional Magento security.
- Log in the Admin Panel and go to Stores > Configuration
- Click Advanced section, then click on Admin
- Expand the Admin Base URL section.
- Set Use Custom Admin URL to “Yes”.
- Enter the custom admin URL
- You will be logged out and redirected to the new Admin URL.
Alternatively, you could enable the “Use Custom Admin Path” field and enter the custom admin path instead of the entire URL.
b. Limit Access to the Admin
More the number of users have access to the admin panel, the more possible points of vulnerability there are. Limit user access to only what is required. For example: an intern does need to know all your sales data. To restrict user privileges for Magento security follow these steps:
- Go to System > Permissions > User roles
- Click on Add new roles
- Enter Role name and passwords
- Go to Role resources
- Select the resource access you wish to grant your new user
- Click on save role.
- Now when you add new users you can select specific role to allow access to only specific resources.
c. Use 2-Factor Authentication For Admin Logins
Multi factor authorization boosts Magento security. Two-factor authentication (2FA) reduces the risk of brute-force attacks and unauthorized access.
Earlier users had to use extensions to integrate 2-factor authentication with admin login. With Magento 2.3 this feature is available out-of-the-box.
2. Use Updated Software
a. Latest Version of Magento With All Latest Security Patches
Magento has security conscious developers who regularly release security patches and updates to check potential and existing vulnerabilities. All you have to do is to install these Magento 2 security patches from time to time to be safe. Keeping your Magento up-to-date is an important step to ensuring Magento security. Follow these steps to upgrade Magento:
1. Before making any changes back up code and database.
2. Use SSH to login to remote server
3. Change to your Magento root directory and set the upgrade version using the version constraint syntax. Composer require:
4. Update the project."magento/magento-cloud-metapackage":">=CURRENT_VERSION <NEXT_VERSION" --no-update
5. Add, commit, and push code changes.composer update
git add -A $git commit -m "Upgrade" git push origin
6. Wait for the deployment to complete
7. Verify Magento version.
php bin/magento --version
b. Update Extensions
Choose third-party extensions carefully. And, keep the extensions up-to-date. Older versions with publicly known vulnerabilities could jeopardize Magento security. Here is how you can upgrade third party extensions in Magento:
- Before making any changes, create a new branch on your local workstation.
- Disable your extensions as needed.
- When available, download extension upgrades.
- Install the upgrade as documented by the third-party documentation.
- Enable and test the extension.
- Add, commit, and push the code changes to the remote.
- Push to and test in your Integration environment.
- Push to the Staging environment to test in a pre-production environment.
For detailed guide refer: Magento upgrade overview
3. Strict File Permissions
Use the strict file permissions. This could prevent illegitimate users and hackers from tampering with important files. Magento 2 recommends that core and directory files should be set to read only, including app/etc/env.php equivalent to app/etc/local.xml for Magento 1.9.
777 give read, write and execute permissions to all users. This file permission should always be avoided. 640 permission means the owner can read and write, the group can read but other users have no permissions. 640 is the recommended permission for all files, whereas 755 permission for all folders.
Review your server for “development leftovers.” Make sure there are no accessible log files, publicly visible .git directories, tunnels to execute SQL, database dumps, phpinfo files, or any other unprotected files that are not required, and that might be used in an attack.
4. Regularly Back Up Data
Ensure that your server and database are automatically backed up to an external location. A typical setup requires daily incremental backups, with a full backup on a weekly basis. Make sure to test the backup regularly to verify that it can be restored.
A working backup will save you a lot of time and effort in case of a malware attack. You can simply get the backup up and running instead of having to write the website code from scratch.
To back up your Integration environment database and code:
1. Create a local backup of the remote database by typing this in your SSH. magento-cloud db:dump (This is only for Magento cloud, and won’t work for most of the self-hosted magento sites).
2. Use this command to back up the file system and database on your website. bin/magento setup:backup --code --db
To back up your Staging or Production environment database before deploying. Create a database dump.
See Snapshot and backup management.vendor/bin/ece-tools db-dump
5. Activate Web Application Firewall
Web Application Firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. This disallows bad bots, malicious users, and blacklisted IP to enter your website. Thereby, providing a layer of security.
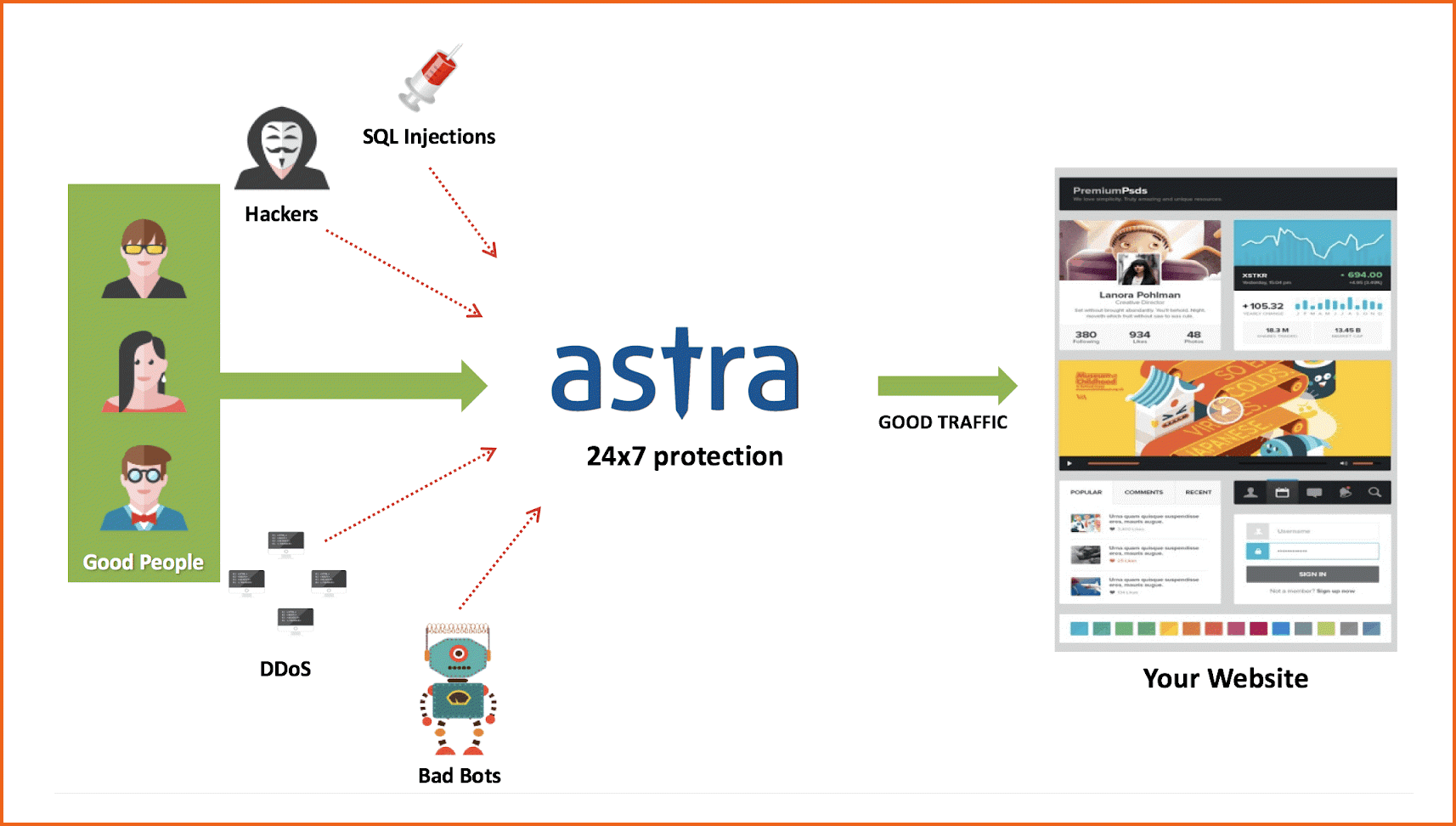
Astra Security’s intelligent firewall protects against 100+ different types of attacks. With IP blacklisting feature, spam blocking, brute force protection make it one of the most effective and cost-efficient firewalls in the market.
6. Disable Dangerous PHP Functions
Some PHP functions are dangerous. They could be used to inject malicious code into your website. It is best to disable them. To disable dangerous PHP functions in Magento for additional security follow these steps:
1. Open the php.ini file on your server
2. Enter the following code
disable_functions = “apache_child_terminate, apache_setenv, define_syslog_variables, escapeshellarg, escapeshellcmd, eval, exec, fp, fput, ftp_connect, ftp_exec, ftp_get, ftp_login, ftp_nb_fput, ftp_put, ftp_raw, ftp_rawlist, highlight_file, ini_alter, ini_get_all, ini_restore, inject_code, mysql_pconnect, openlog, passthru, php_uname, phpAds_remoteInfo, phpAds_XmlRpc, phpAds_xmlrpcDecode, phpAds_xmlrpcEncode, popen, posix_getpwuid, posix_kill, posix_mkfifo, posix_setpgid, posix_setsid, posix_setuid, posix_setuid, posix_uname, proc_close, proc_get_status, proc_nice, proc_open, proc_terminate, shell_exec, syslog, system, xmlrpc_entity_decode”
This code includes names of all potentially dangerous PHP functions. Depending on your server configuration, you may have to restart Apache/Nginx.
7. Install a Security Plugin
Security is a round-the-clock job. Hackers keep finding new ways to penetrate into your system. Security threat landscape is ever changing and it is recommended that you leave the security matters to the experts in the field.
A security plugin will help you keep and eyes on your website while you focus on building your business. Astra’s easy-to-use security plugin comes with several features that ensure 360 degree protection of your online business. It includes features like:
- Blacklist monitoring
- IP blocking
- Country blocking
- Protection against bad bots
- Prevent SQLi, XSS, bruteforce and 100+ other Magento security threats
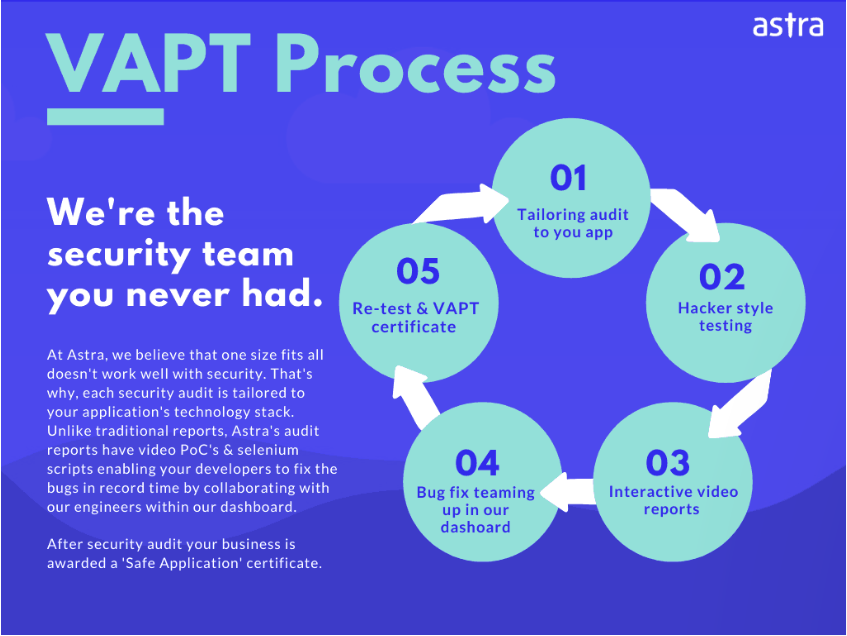
8. Conduct a Security Audit
A security audit tests the security infrastructure around your Magento website. The vulnerabilities found are used for Penetration testing. Pen testing involves exploiting the vulnerabilities (with the owner’s permission, of course!)
Each audit is followed by a comprehensive VAPT report. This report comprises all the vulnerabilities in your website and their possible fixes. Astra Security Audit gives you a complete picture of your website’s security lapses and helps you fix them before hackers get a chance to exploit them.
9. Protect Your Server
1. Use HTTPS / SSL connection while communicating with the server. This ensures secure communication.
2. Do not install extensions directly on a production server. To disable the Magento Connect downloader on the production site, either remove or block access to the /downloader directory. You can also use the same whitelisting methods.
3. Make sure there are no accessible log files, publicly visible .git directories, tunnels to execute SQL, database dumps, phpinfo files, or any other unprotected files that are not required, and that might be used in an attack.
4. Avoid running other software on the same server as Magento, especially if it is accessible from the Internet.
5. Disable directory indexing
10. Things To Do When You Are Hacked
In case your Magento site/store is hacked you can follow these steps to take an immediate action.
1. Take the site offline. Display a polite message to your visitors.
2. Backup the current site. This will include evidence of the installed malware or compromised files.
3. Try to determine the scope of the attack.
4. If possible, wipe and reinstall everything. Malware might be hidden in an unsuspected location and could surface again. Remove all unnecessary files. Then, reinstall all required files from a known, clean source such as files from your own version control system, or the original distribution files from magento.com.
5. Update all credentials
6. Apply latest Magento 2 security patches
11. Develop a Disaster Recovery Plan
In case of a security breach or unavailability of your digital resources, you should always enforce your disaster recovery strategy to get your online entities back online and available to your customers. If you don’t have a disaster recovery (DR) strategy/plan, you can follow these guidelines to make an effective DR plan and mitigate a risk of unavailability:
1. Always take a full backup of your servers and other resources rather than a partial one.
2. Keep a hardcopy of technical information related to your online business setup, this will help in fixing issues that caused a disaster.
3. Communicate with your internal team in case of any disaster. Also, create a list of emergency contact persons in your team to handle such instances.
4. Make a statement ready for your customers to inform them about your business unavailability and also inform them when you’re back online.
5. Protect confidential data of your employees and customers.
6. Practice your DR plan with regular drills and identify holes in your recovery procedures.
If you need any professional help, it’s better to get in touch with a Magento 2 security expert to assist you in identifying the security loopholes. Before restoring the website conduct a thorough vulnerability assessment and penetration testing to prevent future disasters.
Conclusion
Security is ever-evolving. No step guarantees 100% Magento security. But, following these steps would considerably reduce the risk of a hack or a breach. For detailed security plans for your Magento website, get in touch with our security partner Astra Security.
That’s it for this tutorial. If you have any issue regarding this article, then ask our expert Magento support team
Magento Tutorials You Might Be Interested In:

